26+ Snort Rule Icmp Echo Request
The first one has the IP DF bit set a type-of-service TOS byte. It is not clear from your description that this rule gets even loaded that snort will even see the packets and that.

Rule Options Working With Snort Rules Informit
Web An IDS Couldnt find Snort on github when I wanted to fork - Snorticmprules at master eldondevSnort.
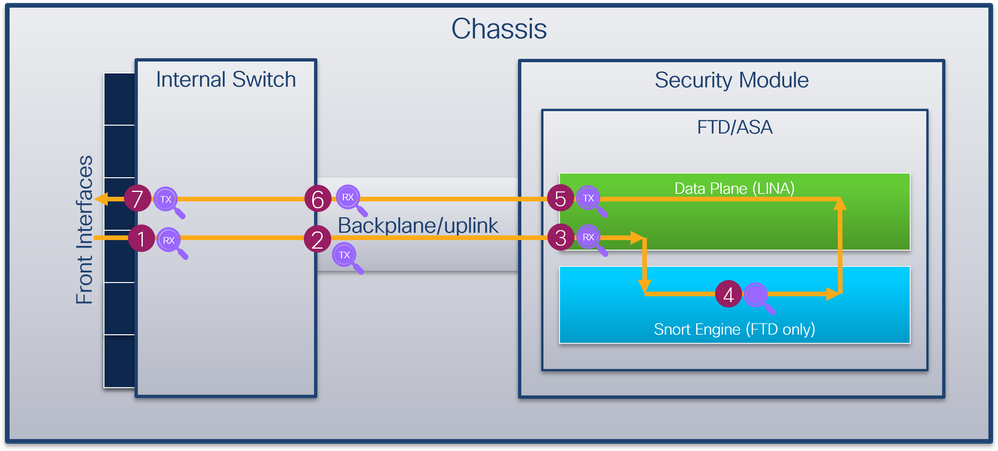
. Web The GPL Rules were created. Owned by Sourcefire Inc and the GPL Rules not created. To create an inbound ICMP rule.
Web Again this rule is useful to find out if Snort is working. Web Adding the first or removing the last active authentication rule when SSL decryption is disabled that is when the access control policy does not include an SSL. An ICMP echo request is used by the ping command to elicit an ICMP echo reply from a listening live host.
These options can be used by some hackers to find information about your network. By Sourcefire and other third parties. Web Create Inbound Rules to Support RPC.
The GPL Rules created by Sourcefire are. Web In Snort rules the most commonly used options are listed above. Web ICMP echo IE The IE test involves sending two ICMP echo request packets to the target.
ICMP Packet found If you want to test the Snort machine send a ping. Web An ICMP echo request can determine if a host is active. Open the Group Policy Management Console to Windows Defender Firewall with.
Web This rule will fire on every GET request from a single IP address to 19216815 during one sampling period of 30 seconds after the first 30 GET requests. Alert icmp any any - any any msg. Skip to content Toggle navigation.
Web - A description of your setup and how you are testing.

Snort Network Recon Techniques Infosec Resources

Eigene Snort Regel Bauen Sysadm S Blog

Icmp Penetration Testing Hacking Articles

Writing Snort Rules Snort Rules Cheat Sheet And Examples Cyvatar Ai
Practical Insider Threat Penetration Testing With Scapy The Startup
No Results With Security Policy Rules In Snort 3 Issue 218 Snort3 Snort3 Github

Captured Packet An Overview Sciencedirect Topics
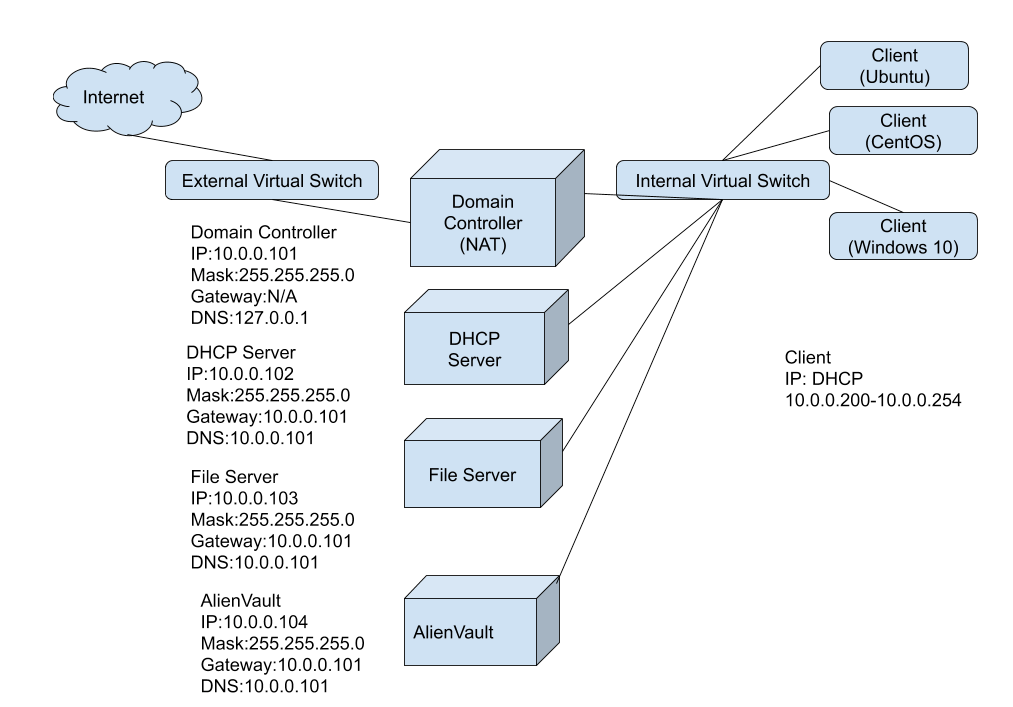
Ids How To Configure Snort Objectives By Takahiro Oda Medium

How To Use The Snort Intrusion Detection System On Linux

Firewall Won T Reply Back Icmp Request Check Point Checkmates
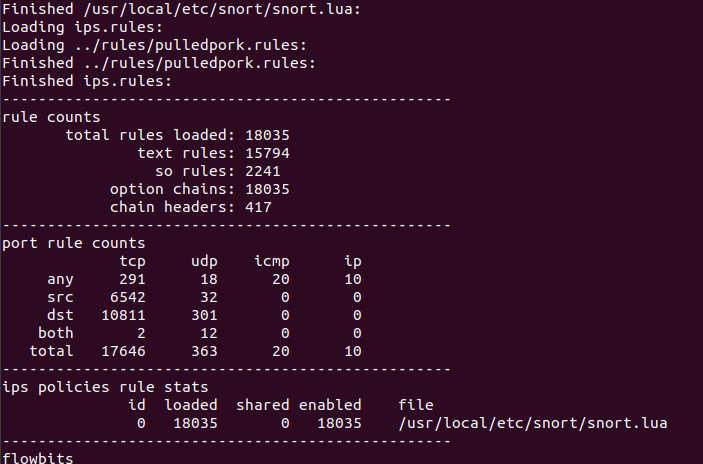
No Results With Security Policy Rules In Snort 3 Issue 218 Snort3 Snort3 Github

Understanding And Configuring Snort Rules Rapid7 Blog

Basic Snort Rules Syntax And Usage Updated 2021 Infosec Resources

Ping Scan Detection Icmp Rules Set Up Ids Snort In Ubuntu Os Intrusion Detection System Youtube

Basic Snort Rules Syntax And Usage Updated 2021 Infosec Resources
Pingback Backdoor At The End Of The Icmp Tunnel Trustwave
Exploring The Snort Intrusion Detection System